Hybrid IT is a combination of on-premise IT and cloud computing. It has become deployed increasingly as companies focus more on the cost, efficiency and security of their IT operations.
According to Cisco’s 2022 Global Hybrid Cloud Trends Report, 82% of the IT leaders surveyed have adopted hybrid IT. The report was based on 2,500 IT leaders from 13 countries and focused on cloud computing, DevOps and enterprising networks. In a similar trend, Gartner analysts estimated that over 85% of companies will embrace a cloud-first approach by 2025. From both reports, it shows the growing adoption rate of cloud technology among organisations globally.
The reason for the shift could be that companies are investing more to improve efficiency and security and a hybrid IT model is seen as a solution. The insights into efficiency and security can be seen from statistics on cloud computing, data breaches, information security and compliance.
For cloud computing, governments and businesses are heading towards future proofing operations and adopting a model such as hybrid IT may be seen as a solution. Techwire Asia reported that the APAC region contributed 14% of global cloud spending. The report further explained that the rapid expansion in APAC was due to digitalisation efforts by governments and companies wanting to forward-compatible operations.
As more industries adopt cloud technology, the organisation’s risk profile changes as more data is being transmitted/transferred to cloud which becomes a target for cyberattacks. For example, data breach is becoming a growing concern especially among companies in Asean markets. According to International Business Machines Corporation, (IBM), in 2022, the Asean region recorded an all-time high of US$2.87 million in the average cost of data breaches per company, which was up 8% from 2021. The report conducted interviews to companies impacted by data breaches to determine the cost to companies that were affected directly to both, the immediate and prolonged response, to the data breaches. This shows that the businesses in the Asean region continue to suffer huge financial losses due to data breaches and highlights the need to prioritise security measures to reduce the likelihood of such an attack.
This requires a different approach to security measures when compared to the traditional on-premise model. With some on-premise setups, data is stored in one location. A single ransomware or DDOS attack may impact the entire data stored in that location. Also, updates, patches and trouble-shooting are managed in-house and the manual process involved in managing security can sometimes be prone to human error.
With the hybrid IT model, companies can store sensitive data on cloud, where it is protected by advanced security measures, such as encryption and multi-factor authentication often found as standard features from cloud service providers. In practice, notable cloud service providers have pre-equipped security protocols and obtain third party validation to meet global compliance requirements. Cloud providers such as AWS, Google, Oracle and others follow the highest global standards of compliance even if these exceed lower, local requirements.
Another advantage in the hybrid IT model is the ability to provide organisations with enhanced disaster recovery capabilities and this relates back to future proofing efforts by companies and governments for the purpose of business continuity. With on-premise IT, organisations may rely on physical backups, which can be time-consuming. With hybrid IT, organisations can use cloud-based backup solutions to quickly and securely back up their data, reducing the risk of data loss and downtime.
The data flow in a hybrid IT model is between the on-premise system and public cloud. Ensuring a secure connection between the on-premise systems and on cloud is critical in protecting the environment from potential attacks. It is applying the right encryption technologies to protect the data in transit and having proper monitoring tools.
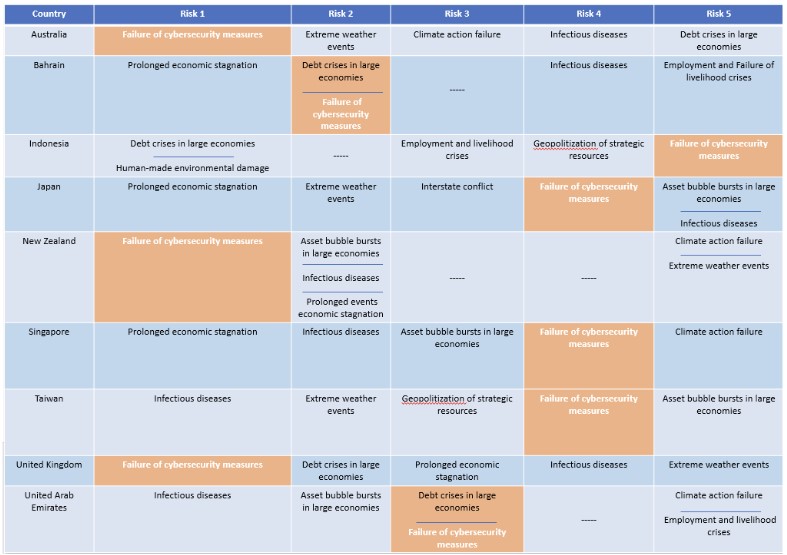
All the security considerations mentioned above can be categorised under information security which is the practice of protecting and securing sensitive data/information from unauthorised access, modification or destruction. A compliance framework can provide structure to a set of security guidelines applicable to an organisation. The World Economic Forum (WEF) – The Global Risks Report 2022, identified the number one risk for Australia, New Zealand and United Kingdom as the “failure of cybersecurity measures”, which was defined as “business, government and household cybersecurity infrastructure and/or measures outstripped or rendered obsolete by increasingly sophisticated and frequent cybercrimes, resulting in economic disruption, financial loss, geopolitical tensions and/or social instability in those countries.” Bahrain, Indonesia, Japan, Singapore, Taiwan and United Arab Emirates were among the list of other countries where failure of cybersecurity measures was ranked within the top-5 risk bracket.
Top-5 Risks Identified by Survey
Table 1: The table of selected countries from Asia, the Middle East and Europe where “failure of cybersecurity measures” was listed as the top-5 risks based on a survey conducted by World Economic Forum’s Executive Opinion Survey (EOS). The participants were asked to select from a list of 35 risks.
With this in mind, all parties in Hybrid IT – both the organisation (customer) and cloud service providers – have a role to play to ensure the risk of security breaches for hybrid IT networks are kept at a minimum by implementing the right measures. The client, in this case usually the enterprise organisation, is required to ensure that the internal processes and information security protocols follow best practices. The client can obtain accredited certifications such as ISO and/or NIST (National Institute of Standards and Technology) for compliance purposes. ISO 27001 is the international standard for best-practice information security management systems (ISMS) while NIST has a similar checklist for information security called NIST RMF (Risk Management Framework). Staff training and operational security are other vital steps in ensuring that related areas of IT security are covered.
Organisations may consider other cybersecurity measures when looking at improving their information security posture. This include access control, firewalls, anti-virus, intrusion detection and prevention system (IDPS), virtual private networks and security information and event management (SIEM). IBM defines SIEM as a security solution that detects potential security threats and vulnerabilities before it can cause any harm to the system. Due to its cost and manpower involved in some setups, SIEM is usually adopted by large corporations, banks and related government departments but there are solutions that cater to smaller organisations.
In conclusion, efficiency and security are becoming top of mind among corporations globally with the wide adoption of cloud technology. But understanding the hybrid IT model when it comes to security and applying the right measures should be a priority to ensure the rate of successful attacks are kept at a minimum. There are many areas in how security can be effectively applied in this environment with some of the basic strategies explained here. As hackers become more complex and advanced in their method of attack, security is forced to continuously adapt to prevent the attack because what is applicable today, may not be tomorrow. Therefore, understanding the risk profile in the hybrid IT model will better prepare organisations for the future.